Διαρροή Δεδομένων: Εκατομμύρια Προσωπικά Στοιχεία Χρηστών του Uid.me
Κίνδυνος Ασφάλειας WiFi: Απειλούνται Δισεκατομμύρια Χρήστες Android και
Σοκαριστική Διαρροή: Περισσότερα από 1,3 Εκατομμύρια Αρχεία της
Η Kyivstar Ανακτά τις Υπηρεσίες μετά από Κυβερνοεπίθεση:
Θρίαμβος για τη BlackBerry: Ανακοινώνει Απροσδόκητα Κέρδη Χάρη
Πολιτικές Εντάσεις: Πώς η Apple Αντιμετωπίζει Κατηγορίες για
Επίθεση Χάκερ Στο Δικαστικό Σύστημα της Αυστραλίας: Κλοπή
Κυβερνοεπίθεση Ransomware Παραλύει Ιταλική Δημόσια Διοίκηση
Επίθεση Χάκερ στη MongoDB:Παραβίαση δεδομένων πελατών
Κυβερνοεπίθεση Στο Δικαστικό Σύστημα της Ελβετίας: Πιθανή Επίθεση
Κυβερνοεγκληματίες Στρέφονται στα Email για Χριστουγεννιάτικες Απάτες
Κυβερνοασφάλεια στην Κίνα: Προειδοποίηση για Κατασκοπευτικό Λογισμικό σε
Απαγόρευση TikTok: Δικαστικές Αποφάσεις Στο Texas και Στην
Διαρροή Δεδομένων: Εκατομμύρια Προσωπικά Στοιχεία Χρηστών του Uid.me
Το Uid.me είναι ένα εργαλείο δημιουργίας ιστοσελίδων που δημιουργήθηκε από τη ρωσική τεχνολογική εταιρεία uCoz. Με κεντρικά γραφεία στη Μόσχα,...
Διάβασε εδώΚίνδυνος Ασφάλειας WiFi: Απειλούνται Δισεκατομμύρια Χρήστες Android και
Δισεκατομμύρια χρήστες Android σε όλο τον κόσμο ενδέχεται να επηρεαστούν από μια νέα ευπάθεια στο WiFi, την οποία οι χάκερ...
Διάβασε εδώΣοκαριστική Διαρροή: Περισσότερα από 1,3 Εκατομμύρια Αρχεία της
Περισσότερα από 1,3 εκατομμύρια αρχεία της Insomniac Games, η οποία ανήκει στη Sony (6758.T), συμπεριλαμβανομένων σχεδίων παιχνιδιών, προϋπολογισμών και πληροφοριών...
Διάβασε εδώΗ Kyivstar Ανακτά τις Υπηρεσίες μετά από Κυβερνοεπίθεση:
Το μεγαλύτερο κινητό πάροχο υπηρεσιών τηλεφωνίας της Ουκρανίας, η Kyivstar, ανακοίνωσε την Τετάρτη ότι έχει αποκαταστήσει όλες τις υπηρεσίες της...
Διάβασε εδώ Hacking Tutorials
Hacking Tutorials Bluetooth Hacking, Μέρος 1: Ξεκινώντας με το Bluetooth
Σήμερα, το Bluetooth είναι ενσωματωμένο σε σχεδόν όλες τις συσκευές και gadgets μας. Στους υπολογιστές μας, τα smartphones, τα iPods,...
 Hacking Tutorials
Hacking Tutorials Επίθεση brute force μέσω XML-RPC σε WordPress
Το XML-RPC (XML Remote Procedure Call) είναι ένα πρωτόκολλο επικοινωνίας που επιτρέπει σε εφαρμογές να επικοινωνούν μεταξύ τους μέσω του...
 Hacking Tutorials
Hacking Tutorials Πως θα βάλετε backdoor σε μια ιστοσελίδα με τη χρήση του Weevely
Συχνά, θα έχετε τη δυνατότητα να ανεβάσετε ένα αρχείο σε ιστότοπο, όπως ένα αρχείο Word, ένα PDF ή μια εικόνα...
 Hacking Tutorials
Hacking Tutorials Η Σκοτεινή Πλευρά των Exploits: Προκλήσεις και Προστασία
Τα exploits αντιπροσωπεύουν μια σημαντική πτυχή του κυβερνοχώρου, καθώς αναδεικνύουν τις ευπάθειες στο λογισμικό, τα λειτουργικά συστήματα και τις εφαρμογές....
 Hacking Tutorials
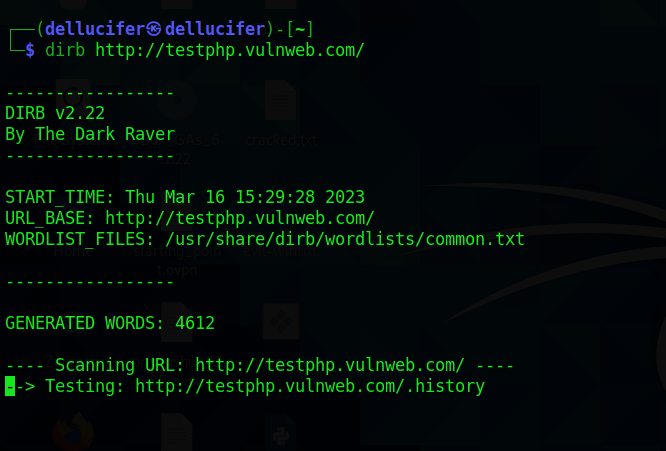
Hacking Tutorials Χρησιμοποιώντας το Dirb για εντοπισμό κρυφών φακέλων και αρχείων σε ιστότοπους
Το Dirb είναι ένα εργαλείο ανοικτού κώδικα για την εξερεύνηση καταλόγων σε ιστότοπους. Πρόκειται για ένα εργαλείο σάρωσης καταλόγων (directory...
 Hacking Tutorials
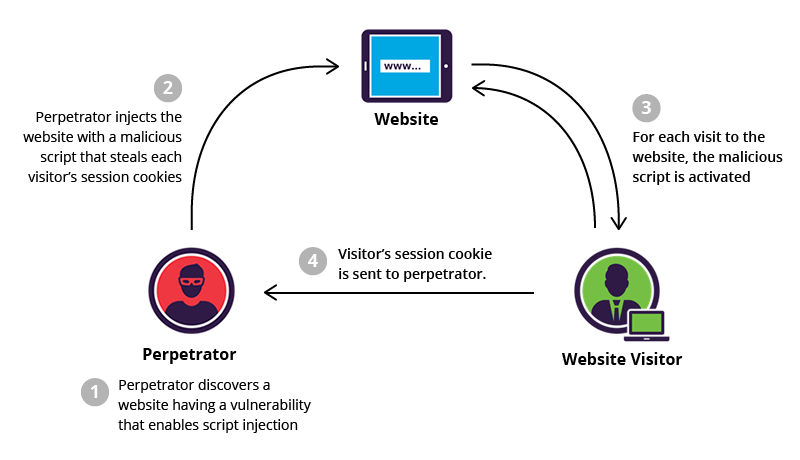
Hacking Tutorials Τι είναι το XSS
Το XSS (Cross-Site Scripting) είναι μια επίθεση κατά της ασφάλειας των ιστοσελίδων, κατά την οποία ο επιτιθέμενος ενσωματώνει κακόβουλο κώδικα...
Buffer Overflow (part IV)
Ήρθε η ώρα να προσπαθήσουμε να εκτελέσουμε buffer overflow (με ανακατεύθυνση) σε ένα λειτουργικό σύστημα Windows 11. Για να δούμε...
Buffer Overflow (part III)
ShellCodes In hacking, a shellcode is a small piece of code used as the payload in the exploitation of a...
Buffer Overflow (part II)
0x0. Εισαγωγή A buffer overflow (bof), or buffer overrun, is an anomaly whereby a program, while writing data to a...
Buffer Overflow (part I)
Το συγκεκριμένο άρθρο είναι το πρώτο μέρος μιας σειράς που θα περιγράψει την αδυναμία Buffer Overflow. Σε αυτό το πρώτο...
Τι είναι το Spoofing; Πώς λειτουργεί και πώς να το αποτρέψετε
Το spoofing είναι μια κακόβουλη εφαρμογή που συγκαλύπτει μια νόμιμη πηγή για να αποκτήσει ευαίσθητες πληροφορίες ή για να αποκτήσει...
Αλλαγή Διεύθυνσης MAC με το Macchanger στο Kali Linux
Το Macchanger στο Kali Linux αποτελεί ένα ισχυρό εργαλείο που επιτρέπει στους χρήστες να αλλάξουν τη διεύθυνση MAC της δικτυακής...
Whoami: Παραμείνετε ανώνυμοι στα Kali Linux
Στη σημερινή ζωή, είμαστε περιτριγυρισμένοι από πολλά εργαλεία ασφάλειας και ανωνυμίας τα οποία υπόσχονται να μας παρέχουν κάποια προστασία. Αλλά...
Οδηγός για πλήρης ανωνυμία στο διαδίκτυο
ΣΗΜΕΙΩΣΗ Αν σας ενδιαφέρει η προστασία της ιδιωτικής ζωής στο Internet τότε πρέπει να πάρετε αυτόν τον οδηγό πολύ σοβαρά. Το παραμικρό λάθος,...
Proxy vs VPN – ποιο είναι το καλύτερο για εσένα;
VPN ή Proxy: Ποια είναι η Καλύτερη Επιλογή; Καθώς η ψηφιακή ασφάλεια και η ιδιωτικότητα στο Διαδίκτυο γίνονται όλο και...
Οι Καλύτερες Μηχανές Αναζήτησης για Ανώνυμη Περιήγηση
Υπάρχουν πολλές μηχανές αναζήτησης που έχουν ως κύριο χαρακτηριστικό την προστασία της ανωνυμίας των χρηστών και τον σεβασμό της ιδιωτικής...